Single sign-on(SSO), is one of the features offered by Azure Directory. You can use SSO on devices, apps, and services from anywhere in the world.
Joining devices to Azure AD assures the corporate devices are protected and that they follow the compliance standards set by the organization.
Users can bring their own devices and join them to Azure Directory and administrators make sure that these devices also follow the standards of your organization.
Let’s have a look at the benefits of Azure AD Join.
Azure AD Join has the following benefits:
Single Sign-On; This is the primary feature of AD Join; you can sign-in
to any of your applications and services without a username and password prompt. The best part is that, is not necessary to connect to the domain network to use SSO.
Enterprise Client Roaming ; The settings are synchronized across devices that are joined to Azure AD.
Microsoft Store for Business; Joining your device and signing-in
to the store with work or school accounts gives you a customized catalog of applications that are shared by your organization.
Windows Hello; This provides you with biometric authentication using facial recognition or fingerprints to access corporate resources and sign-in to devices. The devices should have hardware that supports Windows Hello to use this feature.
Block Access Administrators can enforce policies and devices that do not meet the requirements can be easily blocked.
Let’s see what connection options are offered by Azure AD Join.
Connection Options
You can connect your devices to Azure AD using the two following options:
1)Register your device to Azure Directory Registration creates an identity for the device, and this identity can be used for authentication. Whenever a user signs in, the identity of the device can be used for authentication. Administrators have the right to enable or disable this identity.
2)Join your device to Azure Directory Joining your device provides the same features as registration and additionally changes the local state of the device. With a change of local state, users can sign in to their device using their work or school account. Joining is more like an extension to the registration process.
Combining the registration process with Microsoft Intune (mobile device management [MDM] solution) will help you create conditional policies using the device attribute. Using this combo, you can block devices that do not follow the organizational compliance standards.
For example, you could block all devices that are using Windows XP
or Windows 7 and make Windows 10 the prerequisite for accessing corporate resources.
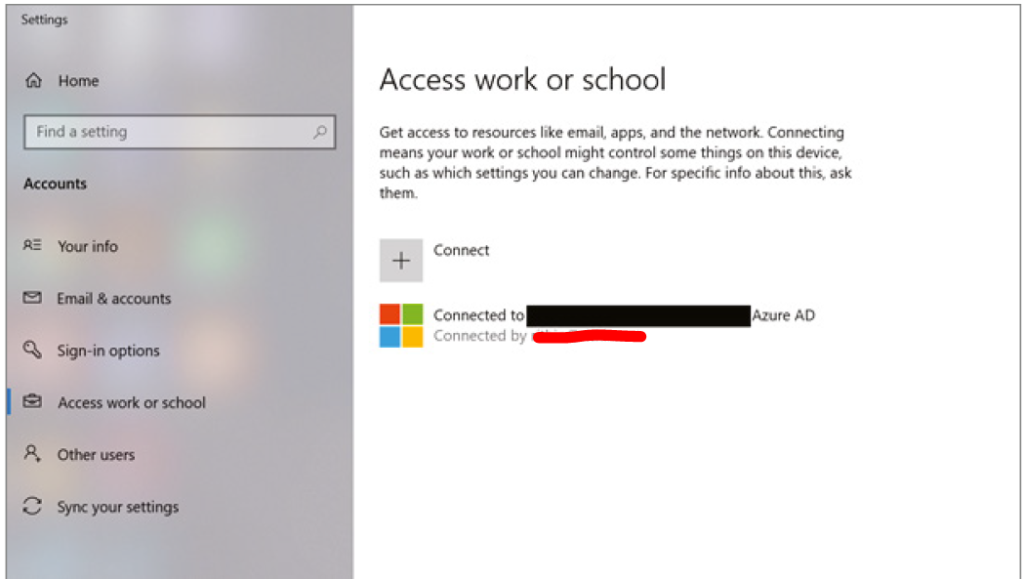
You could join your device to Azure AD by going to your Windows 10
Settings ➢Accounts ➢ Access To Work Or School. Signing in with your work or school account will connect your device to the Azure AD domain, and you can sign in to corporate resources
using SSO.
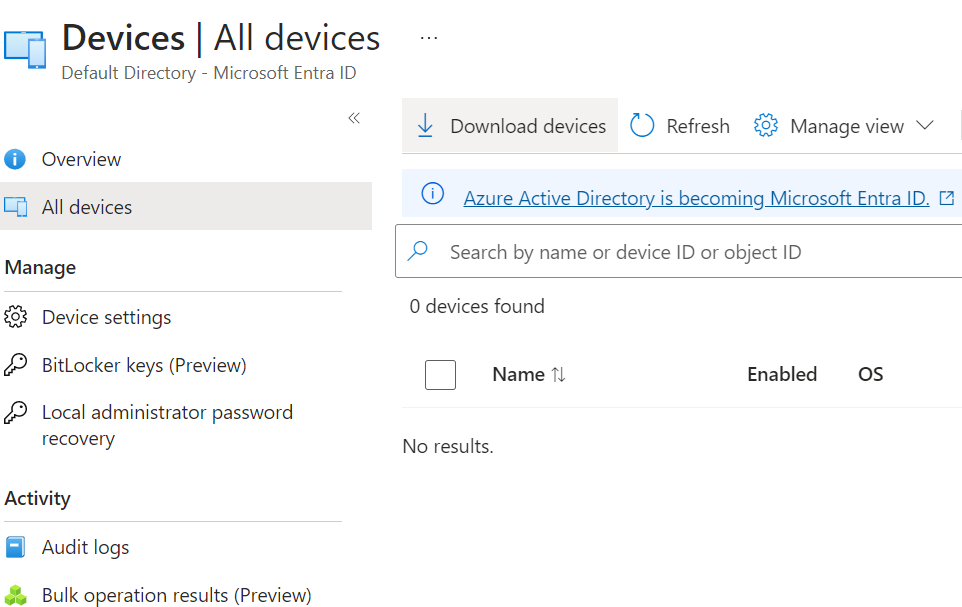
All the devices that are connected to Azure AD can be explored from the Azure Directory ➢ Devices blade.
This blade will show OS information, OS version, join type, and
owner of the devices that are joined.