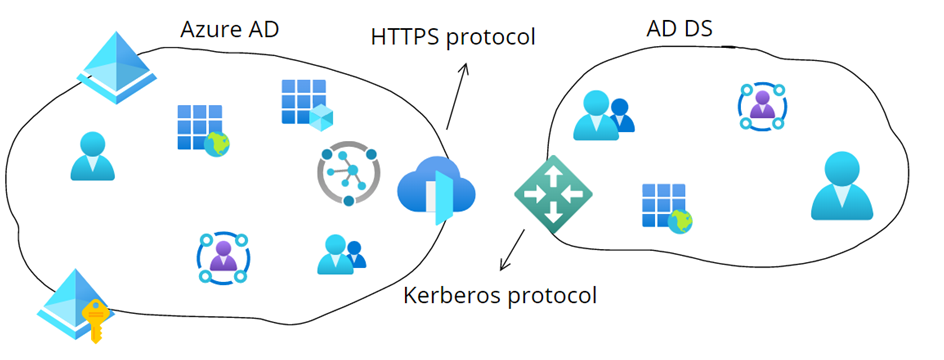
As organizations migrate to the cloud, there can be a lot of
confusion and misconceptions. Cloud governance and compliance
is all about a set of rules that you need to comply with while you are creating, migrating, or managing resources in the cloud.
These rules vary from organization to organization. For example, a government organization may have strict rules that they need to follow when they run a business in the cloud. On the other hand, a private
company will have liberal rules compared to the government one.
Ideally, these rules are no different than the ones you have on-premises;
the only difference is that in the cloud you will be using Microsoft Azure as the platform instead of your on-premises servers.
A lack of rules or controls will create issues with your data privacy, security, and cost, as well as efficiency. With on-premises, you controlled the entire infrastructure, and the perimeter was secured using firewalls and other security devices. In the cloud, you won’t have complete control over the network, so you need to be aware of the vulnerabilities and the
best practices or offerings provided by Azure to resolve them.
Common rules that are followed in organizations are related to data residency, compliance policies like PCI-DSS if you are dealing with customer credit card information, budgeting for cost optimization, and security services to ensure that there are no vulnerabilities that
can be exploited by hackers.
Compliance and governance cannot be achieved in a single day;
This is a continuous process. The policies and procedures need to be tweaked and evolved as you notice room for improvement. Also, sometimes you need to expand the rules to accommodate
new services. Concisely, cloud compliance is all about setting up rules by which you will be continuously monitoring and amending relevant controls for cost optimization, improving efficiency, and eradicating security risks.
Azure Regions
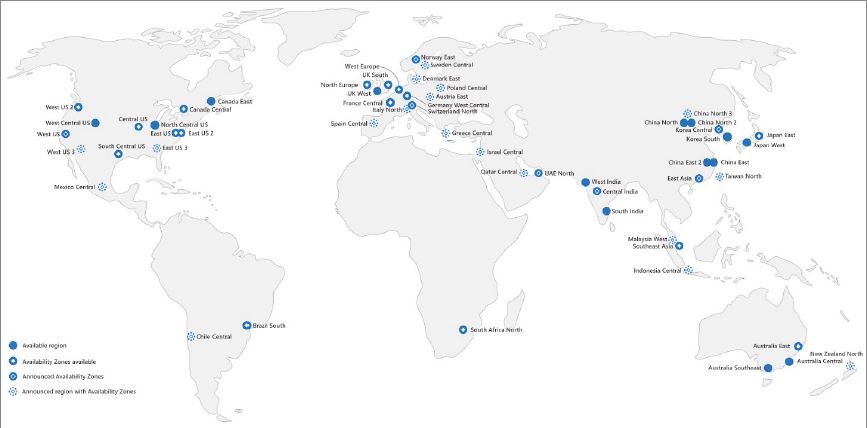
Microsoft Azure comprises data centers that are located across the globe. Currently Azure has more than 60 regions, and there are more in the pipeline.
This global presence makes Azure the cloud provider with the highest number of regions.
Also, this omnipresence gives customers the ability to choose the regions that are right for them. If you are wondering what an Azure region is, a region is a geographical area on the planet comprising at least one data center, but usually multiple. The data centers are isolated
from each other in close proximity and connected to each other via low-latency networks, enabling faster and seamless communication.
East US, Brazil South, UK South, India West, and Australia Central are some examples of Azure regions.
- Regions offer flexibility for customers to deploy resources to regions that are close to their customers.
- Regions ensure data residency for customers.
- Regions offer compliance and resiliency options.
- When you deploy a resource in Azure, in most cases you will be asked to choose a region.
- Certain services are region specific, and the availability is limited to some regions when they are launched. Gradually, Microsoft will expand the service to other regions.
- Services like Azure AD, Azure Traffic Manager, and Azure DNS do not require a region.
- The region for these resources will be shown as Global in the Azure portal.
- Each Azure region is paired with another region within the same geography to form regional pairs.
Regional Pairs
Each region consists of one or more data centers that are in close
proximity and connected via a low-latency network.
Now, an Azure geography is defined as an area of the world that consists of one or more Azure regions. Some examples are United States, India, Asia Pacific, United Kingdom, etc. If we take the United States geography, it consists of several regions such as East US, West US, Central US, etc. So, an Azure geography ensures the data residency and compliance requirements are met.
If you are an organization working with a US government organization, then you cannot store data outside of the United States. Similarly, the European Union has the General Data Protection Regulation
(GDPR) where organizations cannot store personal data of the EU citizens outside EU member states. If your organization is GDPR compliant, you can pick a geography that is within the EU and stay compliant.
Azure pairs one region with another region within the same geography. Regional pairs play a vital role in business continuity and disaster recovery (BCDR). Whenever there is a planned update on the Azure platform, Azure rolls out the update sequentially across regional pairs. This guarantees that only one region in the regional pair is updated at a time
and the other one can be leveraged for the recovery of the services if something goes wrong.