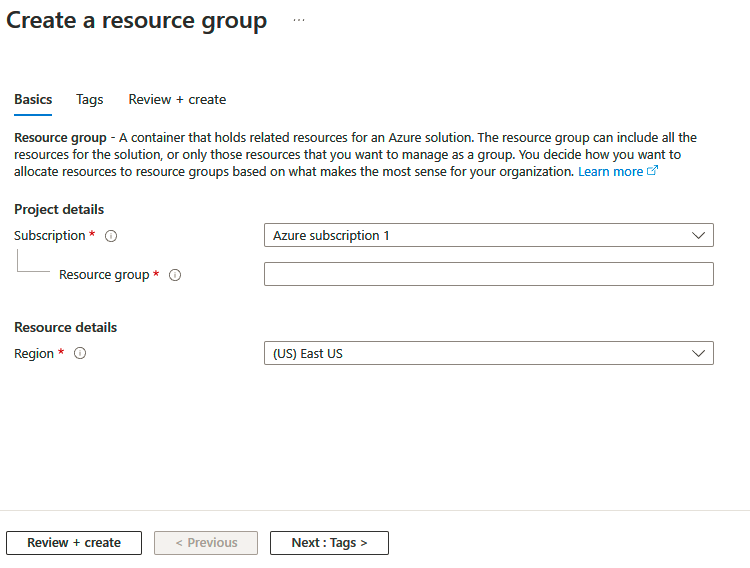
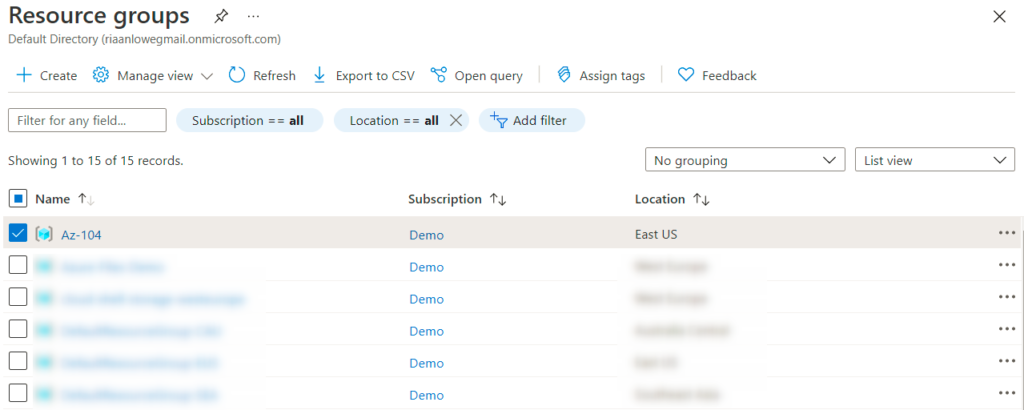
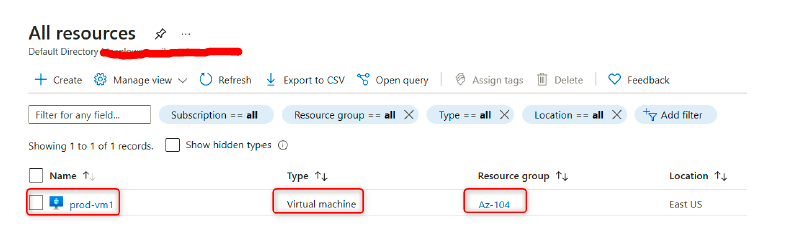
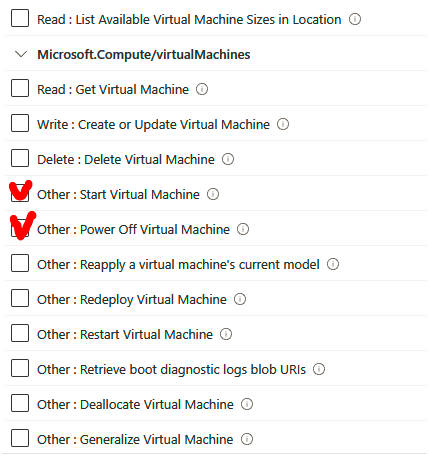
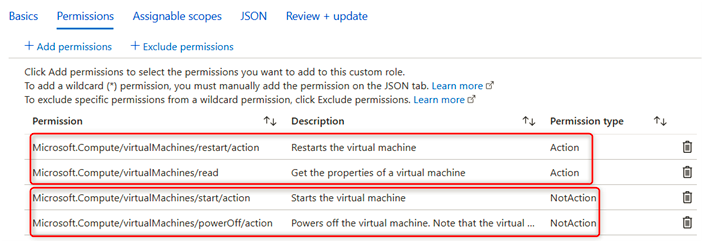
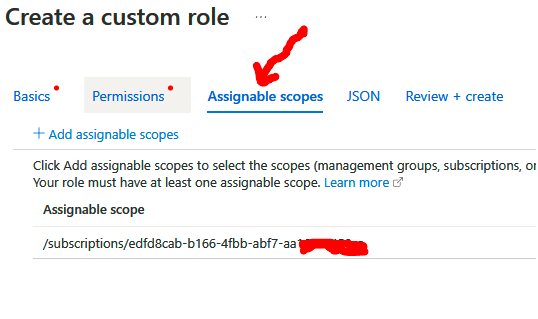
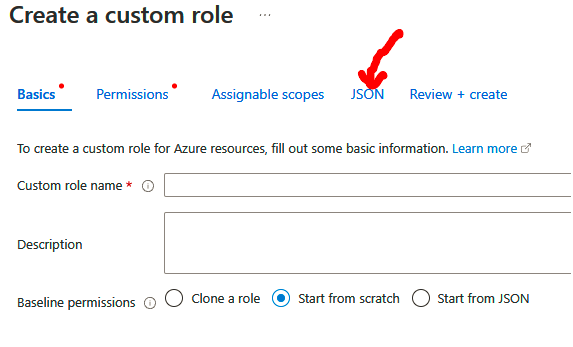
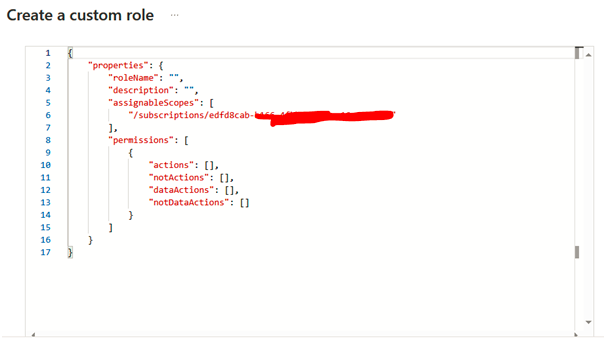
We will explore the different types of storage accounts available to Azure, the different access tiers, disk storage, and the varying redundancy options. We will create a storage account, set up file shares and blob storage, and use Azure Storage Explorer to manage storage accounts. We will also explore how to import and export data from Azure.
Understanding Azure storage accounts
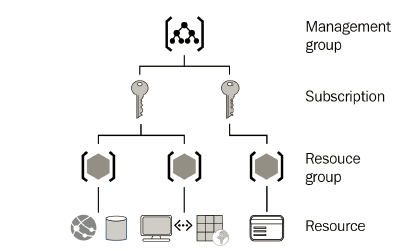
Azure offers a variety of services that can be utilized for storage; these can vary from database options to messaging systems, to files. Azure has identified four core types of services and integrated these into a single service named Azure Storage.
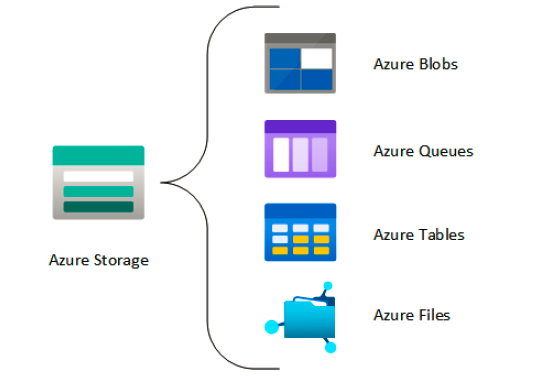
These are identified as Azure Blobs, Azure Files, Azure Queues, and Azure Tables under an Azure storage account. A storage account may contain several data services in a combination of the ones described previously and stored collectively in a grouped service.
Various types of data—such as files, documents, datasets, blobs, and virtual hard disks (VHDs)—can be stored in the storage account, and most will be accommodated by the defined structure. The following screenshot illustrates the different storage services associated with a storage account:
Types of storage accounts
Azure Storage currently offers several different types of storage accounts, as detailed in this section. There are various components to consider when choosing the correct type of account, these being the following:
- Type of storage account (consider the service required)
- Redundancy
- Intended usage
- Performance
- Replication
- Security
- Limitations
Let’s see in detail the different types of storage accounts.
General-purpose version 1 (legacy)
A general-purpose version 1 (GPv1) storage account is the oldest type of storage account. It offers storage for page blobs, block blobs, files, queues, and tables, but it is not always the most cost-effective storage account type.
It is the only storage account type that can be used for the classic deployment model but does not support the latest features, such as access tiers.
This account type is no longer recommended by Microsoft. It is still
generally considered the cheapest of storage options but is highly restricted compared to general-purpose version 2 (GPv2) storage.
Although legacy, these accounts can be upgraded to GPv2 storage. However, you should also consider storage costs as these might
increase as a result of the change.
GPv2
This is a standard storage account and supports blobs, queues, tables, and file shares.
This is the storage account type recommended for most scenarios. It supports locally redundant storage (LRS), geo-redundant storage (GRS), read-access GRS (RA-GRS), zone-redundant storage (ZRS), geo-ZRS (GZRS), and read-access GZRS (RA-GZRS)
redundancy options.
Standard blob storage
Azure Blob storage offers unstructured data storage in the cloud. It can store all kinds of data, such as documents, VHDs, images, and audio files.
There are three types of blobs that you can create. This type of storage is also considered a legacy storage account type and consists of various types of blobs, as outlined here:
- Page blobs: Blobs that are used for the storage of disks. These blobs are optimized for read and write operations and stored in 512-byte pages. So, when you have a VHD that needs to be stored and attached to your virtual machine (Virtual Machine), you will have to create a page blob. The maximum size of a page blob is 8 tebibytes (TiB).
- Block blobs: Basically, these cover all the other types of data that you can store in Azure, such as files and documents. The maximum size of a block is 4,000 mebibytes (MiB) and the maximum size for a blob is 190.7 TiB.
- Append blobs: These blobs are optimized for append operations, basically meaning that data (blocks) is added to the end of a blob. Each block can be of different sizes, up to a maximum of 50,000 blocks. Updating or deleting existing blocks written to the blob is unsupported.
The standard blob storage account offers all the features of StorageV2 accounts, except that it only supports block blobs (and append blobs). Page blobs are not supported.
It offers access tiers that consist of hot, cool, and archive storage, and Microsoft recommends using GPv2 storage instead of standard page
blobs as this is supported without the requirement for limitations. It supports LRS, GRS, and RA-GRS redundancy options.
Example workload types include the following:
- Backup and archiving functionality
- Disaster recovery (DR) datasets
- Media or unstructured data content
Premium block blob storage
Premium storage is used for situations requiring lower latency and higher performance. This is enabled through high-performance hardware associated with the presentation of storage within Azure, such as through solid-state drives (SSDs), and provides faster throughput and input/output operations per second (IOPS) compared to standard storage, which is backed by hard disks (spinning disks).
This storage is typically used for block blobs and append blobs. It supports LRS and ZRS redundancy options.
Example workload types include the following:
- Workloads requiring fast access and functionality, such as e-commerce applications
- Large datasets that are constantly added, manipulated, and analyzed, such as internet of things (IoT) applications
- Artificial intelligence (AI) or machine learning (ML) applications
- Data transformation workloads
Azure file storage
With Azure Files, you can create file shares in the cloud. You can access your files using the Server Message Block (SMB) protocol, which is an industry standard that can be used on Linux, Windows, and macOS devices.
Azure files can also be mounted as if they were a local drive on these same devices as well, and they can be cached for fast access on Windows Server using Azure File Sync. File shares can be used across multiple machines, which makes them suitable for storing files or data that is accessed from multiple machines, such as tools for development machines, configuration files, or log data.
Azure Files is part of the Azure Storage client libraries and offers an Azure Storage Representational State Transfer application programming interface (REST API) that can be leveraged by developers in their solutions.
Premium file shares storage
Premium storage is used for situations requiring lower latency and higher performance.
Premium file shares are typically used for workloads requiring enterprise-scale or high-performance applications. The service presents storage in the form of SMB or Network File System (NFS) storage.
SMB is typically used for Microsoft Windows-type environments such as Windows Server, whereas NFS is typically used for Linux-based
environments. NFS can only be enabled on premium file shares.
Some differences worth noting when choosing your file-share storage service are IOPS and provisioned storage limitations. GPv2-backed file shares have a limit of 20,000 IOPS and 5 pebibytes (PiB) of provisioned storage, while premium file shares storage offers 100,000 IOPS but only 100 TiB provisioned storage.
Storage access tiers
Blob storage accounts use access tiers to determine how frequently data is accessed. Based on this access tier, you will get billed.
Azure offers three storage access tiers: Hot, Cool, and Archive. Azure also offers configuration options for blob life cycle management,
which we will explore more on the next post
Hot
The hot access tier is most suitable for storing data that is accessed frequently and data that is in active use. For instance, you would store images and style sheets for a website inside the hot access tier.
The storage costs for this tier are higher than for the other access
tiers, but you pay less for accessing files. This is the default access tier for storage.
Cool
The cool access tier is the most suitable for storing data that is not accessed frequently (less than once in 30 days). Compared with the hot access tier, the cool tier has lower storage costs, but you pay more for accessing files. This tier is suitable for storing backups and older content that is not viewed often.